When someone impersonates you by exploiting your personal information to perpetrate fraud or gain other financial advantages, this is known as identity theft or identity fraud. Your personally identifiable information includes your name, residence address, email ID, login and passwords, Social Security number, driver’s license number, passport number, or bank number. Once this information is obtained, a person involved in online identity theft may sell it on the dark web or use it to steal people’s identities.
Your personal information can be obtained in a variety of ways, including overhearing you on the phone, reading out your credit card number, buying it on the dark web after a data breach, and other strategies. Utilizing such information is the next stage in the identity theft process.

How does Identity Theft work?
Your personal information may be accessed by identity thieves through a variety of methods. These are a few:
Phishing
Cybercriminals send emails or SMS messages that seem real, and these emails or messages can include links that are dangerous. The software is capable of data leakage and can mine your PC, and cyber criminals use these details to sell or steal identities on the dark web. Never click on links in emails that appear dubious. Additionally, avoid downloading anything from unidentified senders or clicking on any unexpected URLs.
Wi-Fi snooping
Public Wi-Fi connections that are not secure might provide hackers access to the data sent to and from your device. Cybercriminals may track your device and may also infect it with malware.
They will then have access to essential data as a result of this.
Online scammers occasionally create Wi-Fi hotspots under names resembling legitimate or original networks. Data traveling across the malicious network may be visible and usable by identity thieves. Always confirm the network name’s spelling before connecting.
What are the effects of identity theft
Few people are mentally prepared to deal with the consequences of ID fraud. Identity fraud victims may go through excruciating psychological pain as a result of loss, helplessness, resentment, loneliness, betrayal, and even disgrace.
After committing financial theft, you may find getting a loan, keeping your apartment, or finding work challenging. Please understand that if you are the family’s primary provider, you have not let them down. You are a victim who is innocent.
Finally, you risk being frustrated with the individuals you ask for help. The judicial system still requires improvement, and it is difficult to crack the case of identity theft. Be compassionate to people who are attempting to help you as well as to yourself.
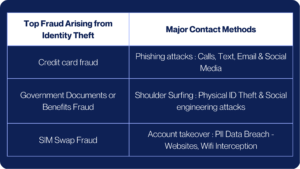
How do Identity Verification & ID checks work?
The theft of identities is increasing. Recent high-profile data breaches affecting millions of customers have made security a significant concern for all companies with access to private customer information. Know Your Customer (KYC) requirements are increasingly being required to include accurate ID verification. Organizations may gain from having the appropriate KYC technology and processes in place by keeping compliant and increasing consumer and client trust that they are taking the necessary precautions to secure their personal information.
Fighting fire with fire, the answer to the ID theft issue is found in the technology that makes it possible. In order to defend themselves and their clients against viruses, spyware, and even conventional methods of ID theft, organizations are arming themselves with technology.
ID verification technology has advanced to assist in better security measures being put in place to minimize identity fraud as it becomes more sophisticated. Before approving a transaction, businesses may now use new technologies to assist them in clearly determining whether a consumer is whom they claim to be.
Let’s discuss how identity verification will become ubiquitous in 2022, reducing fraud and improving consumer experiences.
- Complete incorporation
Companies that create fintech software are increasingly conscious of the critical requirement for tools and systems that ultimately interact with banks’ current core technology. Most businesses are likely to wait to make significant modifications to their core processors any time soon since doing so is frequently too expensive to be justified. Doing so would also be risky if the new iteration operated differently than planned.
The most recent ID-verification solutions were therefore developed with the need to integrate with modern CPUs in mind. Therefore, possible compatibility problems are identified through thorough testing and resolved during the prototype stage of product development. This ensures that ID-verification technology functions appropriately from the moment it is implemented rather than spending months fixing faults brought on by incompatibility problems.
- Streamlined biometrics
With each successive iteration, biometrics gain in strength and are a hot issue in the field of ID verification. Depending on the application, users of biometric technology can confirm their identities using geolocation, social media accounts, fingerprint, iris scan, and face recognition.
Although the technology spreads across sectors, Apple® Inc., a leading innovator in the technology industry, may have had the most influence on consumer acceptance. The business just introduced new fingerprint technology. With the iPhone® 5s, fingerprint recognition technology was used to verify ID and unlock the device. The iPhone X’s facial recognition technology, which claims to distinguish a person’s face from a million others, is expected to surpass the new technology, which had its day in the spotlight.
Convincing people to use the technology if it necessitates a change in their typical behavior patterns is sometimes the most challenging aspect of effectively releasing consumer-facing ID theft technology. It’s essential to remember that, similar to fingerprint ID technology; users will probably become accustomed to facing recognition via regular exposure and use on their devices. Organizations won’t probably use the functionality as part of their ID verification procedures until it has been tested and widely used.
- Consumer concern drives demand for change
On FICO’s most recent consumer finance trend, 44% of American consumers identified ID theft and banking fraud as their top concerns.
- ID theft costs banks 16.8 billion dollars annually, in addition to incalculable losses in client goodwill, so combating it is undoubtedly a significant priority for businesses.
- More efficient identity-verification methods are being developed to suit market demands as consumers and businesses grow more security sensitive.
The confluence of the developments above shows that new technology is catching up to ID security issues, even if they may be rising. The broad adoption of these trends will ultimately result in more secure offline and online interactions, which will be advantageous for both consumers and enterprises.

What are the techniques for secure digital onboarding
The digital client onboarding process is the primary procedure through which businesses and organizations integrate their clients and users in a quick, easy, safe, and assured manner.
This crucial phase of the user-organization relationship is the turning point for two key elements: the security of the business or organization to bring on board a legitimate user with the necessary controls (the customer onboarding process) and the ultimate decision of the prospective client to become a client.
What is the secure customer onboarding procedure?
The process of gaining or subscribing to new customers, ensuring they have access to all the services and products that a company may offer, and integrating them into the database is called onboarding.
So, what exactly is an onboarding procedure? A formal relationship with a person as a registered user or formal client is established through a KYC client onboarding procedure. It is an important stage in determining if the potential customers are suitable to become previous customers of our business or whether it is preferable to reject them. The customer will register with our business. As a result, it offered information that enabled its identification and access to the products and services accommodated.
The phrase “onboarding” is frequently used in any industry where an organization has to integrate a person into its structure, whether as a client, employee, or user, even though the notion is well recognized in human resources and talent management. We will discuss the definition of digital onboarding when this procedure is conducted online.
What is the Digital Onboarding definition in Banking?
This digital onboarding procedure may now be completed online and remotely from any device with a camera thanks to digitalization. Companies in any industry, even those as sensitive as the financial sector, can digitally identify customers to add new clients and users from anywhere, anytime, and through any channel with security and regulatory support. This is made possible by precise and thorough technical and security controls. From the beginning to the end, the onboarding procedure is a remote onboarding experience.
As well-known as Know Your Customer (KYC) or Know Your Client is the process of onboarding customers. These concepts, which are frequently used in the banking, finance, insurance, and related sectors, are occasionally used interchangeably with the term “digital onboarding,” which is used in all fields and businesses. Onboarding is the initial stage in the KYC process, even though KYC includes a more extensive range of processes than onboarding.
Thanks to the development of new digital onboarding systems and creative digital onboarding software platforms and solutions, this procedure may be automated using any digital device.
What are the different types of client onboarding?
- Client Onboarding On-Site: It follows the traditional onboarding process. The consumer must visit a company’s commercial office, branch, or store and provide a valid identification document.
- Semi-On-Site Client Onboarding: Businesses provide digital forms for new clients to complete at home, but they still need to come to the branch to turn them in.
- Online or Remote Onboarding for digital clients: The process of onboarding is entirely digitalized through the use of the software. Customers may now register for services and sign contracts for them remotely with the same security and assurance as they could in person.
Identity Verification with Online Onboarding APIs: How does it work?
Financial services are being transformed by remote KYC onboarding.
Banks and other financial organizations have finally internalized the requirements of today’s clients. Consequently, most of them have changed their onboarding procedures and the entire KYC system to provide consumers with an easy, seamless, and comfortable onboarding experience. Digital client onboarding applications and platforms have thereby assisted in optimizing schedules, resources, and expenses.
AML KYC customer onboarding software makes digital identification entirely online and remote. Customers do not need to travel to obtain and use goods and services: With the new laws and technological advancements created by IDcentral, the remote opening of bank accounts is now feasible with the same assurance and security as face-to-face techniques.
How is Digital Onboarding Transformative for Businesses?
Financial companies have profited from this ground-breaking new technology and its regulatory framework. The user may utilize this technology, which makes a drawn-out and complicated process quick and easy. However, Video KYC enables real-time verification since certain software vendors have integrated machine learning and artificial intelligence into the KYC (Know Your Customer) procedure.
Adopting digital client onboarding solutions has demonstrated that businesses adopting this technology for customer acquisition have drastically enhanced their conversion rates (in other industries, such as insurance). Because this new system conforms with the most robust video verification security standards, clients are also protected against fraud.
How does banking client onboarding work? What are the benefits of online Client AML-CFT screening?
Banking may benefit significantly from digital onboarding. The digital onboarding process is essential for banks in these businesses because it boosts productivity, removes obstacles and wait times, and complies with the most stringent AML and KYC rules while increasing conversion rates and improving user experiences. Similarly, by offering a cutting-edge client onboarding experience, the most advanced banking and FinTech onboarding technology may assist these businesses in meeting the registration process expectations of their customers.
AML5 Directive adoption in their online onboarding procedures has helped many businesses, particularly those in the financial sector, take the lead in the market and gain access to a new European market with 508 million prospective clients.
Solutions and Technology for Customer Onboarding
Live identity verification is a procedure that confirms a person’s or an entity’s identification using real-time data. LIV integrations are most frequently used to confirm a person’s or an organization’s identification during the account opening process. Including LIV in automated workflows can help your financial institution’s LIV operations become more productive.
Reduced risk using Live Identity Verification
The emergence of digital processes has made manual verification insufficient. To reduce friction in the consumer experience, speed and automation are increasingly essential. Identity verification must now be included in automated operations. As a result, operations and confidence may be maintained when firms operate at scale. If you want to achieve this, you need a solution that meets your business goals without materially altering your technical infrastructure or client experience.
Live identity verification for automated account opening processes and KYC compliance workflows
Live identity verification is an attractive solution for KYC compliance and is necessary for commercial bank accounts. Additionally, it’s a terrific method to enhance client satisfaction and offer more value-added services, including mobile banking.
Meeting your consumers where they are is the first step; right now, that place is on their phones. For automated workflows with commercial account opening, it is advantageous to offer live identity fingerprinting so that you may reach your consumers where they are most likely to be: on their smartphones or tablets.
Consider that you have issues with clients whose identities must be verified as part of KYC compliance requirements. Before they can be given the go-ahead to create a commercial account, they must carefully check the documentation provided by each application. Your bank and clients, who may wait days or weeks for their accounts to be established, must invest time and money into the process.
Live capture is the best option in this situation. Live capture can assist in meeting your business account opening and KYC compliance needs since it can rapidly and automatically check the validity of papers using live image processing.
It’s also a fantastic alternative for AML compliance since it ensures that before starting to work on applications, all staff engaged in creating commercial accounts have been confirmed to be whom they claim they are. Also, because live capture occurs immediately after an application enters its information, you can always determine if something odd has happened.
Trust-based Identity Verification Procedure
You can also trust your users by incorporating a trusted identity verification method into your workflow. You rely on a single vendor to manage your authentication. If so, you may be sure that every person they authenticate has been confirmed to be whom they claim to be and has access to the information they want. As a result of this increased confidence and assurance, your staff will feel more certain about their work.
Enable variable levels of verification with identity scoring
Based on the identification information, a person’s risk level is assessed through identity scoring. It’s an excellent approach to decide if you should proceed with human verification, automate the process, or omit the stage altogether.
But before you skip it, remember that identification scoring is designed to be something other than taking the role of human or automatic tests. Instead, it assists in making future choices on how to allocate your resources and what approaches would be most fruitful.
Let’s say you are utilizing a particular service to manage your authentication. In that situation, you can be confident that every person they authenticate has been confirmed to be whom they claim to be and has access to the information they require. The other trust and peace of mind will give your staff more assurance about their work.
Using identity scoring, choose the appropriate degree of verification.
By using identifying information, identity scoring establishes a person’s level of risk.
Standard Features and Types of Live Identity Verification
Consider machine learning, artificial intelligence, and biometrics. These technologies are sophisticated and constantly changing. However daunting these keywords may appear, they are real instruments that assist businesses in confirming the identity of their customers. And considering the prevalence of identity theft and fraud in the digital age, this is becoming more and more crucial.
The typical attributes and variations of identity verification systems are shown below (along with their relevance):
Identity verification with machine learning
The capacity of machine learning IDV to adapt and learn from experience is one of its typical characteristics. Accordingly, it becomes better at identifying which faces belong together and which do not as more individuals go through the process. It also gains knowledge from other data points, such as demographic characteristics.
This kind of technology is frequently utilized for access control applications when several users use the same system throughout the day since it operates in real-time without human assistance (such as in a corporate office). This indicates that they may entirely rely on machine learning instead of having someone sit down each day to add new people’s faces to their system or update current ones.
Identity Verification using biometrics
Verifying an individual’s identity using their distinctive biological traits is known as biometric identity verification. These traits include iris images, speech patterns, hand geometry, face features, and fingerprints.
Biometric Verification has been regarded as one of the most secure ways since another person cannot replicate biometric data.
Verification of identity using artificial intelligence
We’ve all read the headlines warning that AI will rule the planet. That’s what the Internet says, at least. What does that signify, however? Machine learning is a kind of artificial intelligence (AI). The computer software that uses machine learning may learn from experience and predict the future using data that has already been collected.
That might sound straightforward, but since Alan Turing released his article “Computing Machinery and Intelligence” in 1956, our definitions have been clouded by the philosophical debate over whether or not computers are capable of thinking similarly to humans.
Contrary to popular belief, AI has existed for far longer: Every time you ask Siri on your smartphone for directions or make an appointment, AI is at work. Netflix also uses AI to propose movies based on previous viewing habits, and Amazon uses AI to offer products you might enjoy. Google Search utilizes AI to comprehend natural language search terms.
Incorporating live identity verification into automated workflows: What are the steps to take
Including an identity verification service in your automated workflow might be easy. Still, it would help if you first chose which service is appropriate for your company and which key characteristics are most crucial.
First, select the ideal ID verification service for your business.
Make sure to conduct some study before making your decision because there are several possibilities, each with advantages and disadvantages.
Make sure the provider offers a range of alternatives for proving your identity: While some services (like government databases) only offer data from a single source, others (like social media accounts) have access to several sources as well as more complex data like “vouched-for” information. If your company needs more thorough verification than a single source can offer, look for an IDV solution that offers a variety of user access points. Also, remember to consider how the solution will integrate with your workflow.
Step 2 includes picking important features for ID Verification
The following steps assess your organization’s present identity verification capabilities and decide which features you want to use. The list below gives a breakdown of some crucial components to think about:
- Examine ID documents
- Check the user’s identity (or device)
- Check the IP address of the place from where they are visiting your application or website.
- Check to ensure they are utilizing a simple program or website rather than a phony created by hackers to steal critical data.
- Identify any malware that may have infected their operating system and exposed sensitive data.
Integrate ID Verification into Your Workflow in Step Three
- Select a service: It would help if you first decided which ID verification solution is suitable for your company. Several possibilities range from labor-intensive manual services to completely automated ones. The following are some fundamental qualities to take into account:
- Face authentication: Using facial recognition software, which examines critical features of users’ faces and compares them to a database of photos, this technology enables users to confirm their identities.
- Voice recognition: This function compares a caller’s voice with a current database of recognized voices using AI-powered speech recognition software (think Siri or Alexa).
- Tools for fingerprinting: These devices use biometric gear to scan a person’s fingerprints or retinas and compare the results to databases of known fingerprints or retinas, such as security employees at airports or border crossings.
- Device Fingerprinting: Several additional techniques include behavioral analysis (such as comparing how someone handles their smartphone), location verification using GPS coordinates and time zones (such as determining if someone is at home during working hours), etc.
How can live Identity Verification APIs be integrated into existing workflows
As long as you select an excellent provider and consider its capabilities, integrating a live identity verification service into your automated process may be straightforward.
The following steps:
- Select the best service for your requirements. To include the provider in your automated process, you should look for one that provides a variety of checks and has an API available.
- Before enrolling with a service, carefully consider the features offered by each sort of check they provide—for instance, some offer more than simply SSN verification, while others do not offer the opportunity to verify Social Security numbers (SSNs)—and make sure they meet your needs.
With these easy steps, you can get started and ensure that all of your client data is correct and kept safe throughout the process.
Live identity verification in several industries using automated procedures.
While live identity verification is a crucial investment for the banking sector, other sectors quickly embrace the service.
Telecommunications
Telecommunications is one of the most competitive industries that deal with customers. Most clients choose a new provider in a couple of minutes based on initial impressions and brand recognition. Providers need to optimize every client touchpoint, and Identity Verification is the most crucial element. A lengthy and time-consuming SIM Card registration process results in the regrettable immediate clientele loss of many good brands.
If you incorporate mobile Identity Verification into your customer-facing app or website, your users can finish their SIM card registration using their smartphones in a matter of seconds! Your staff will have more time to focus on enhancing customer service rather than recruiting new customers because the process is quick and easy.
This is how it works:
With identity verification, mobile onboarding is quick and secure.
The key to efficient digital onboarding is removing any unnecessary obstacles. Customers may now self-onboard for SIM card registration at their convenience without having to go to a store. Using a mobile-friendly Digital onboarding process, all the necessary information can be quickly collected uniformly and quality-assured.
By integrating mobile data collection into your app or website, new customers can rapidly register new SIM cards and log into their accounts using a mobile device. Using optical character recognition (OCR) technology, the Identity Verification data is digitally gathered and linked in milliseconds to the new SIM card number, which is also scanned using OCR technology.
This streamlined process will save customers and your staff a substantial amount of time, as demonstrated in our mockup video. Your clients may have a painless registration procedure while errors are fixed, and documentation is handled.
A safe and straightforward registration process
Several nations require that your SIM card be linked to your identification. The collected data is shared with the local authorities to ensure that SIM cards are registered to the proper person and cannot be used illegally. As a result, the data collection must be done carefully.
Anyone using mobile data capture may scan IDs and manage data locally without an internet connection. Since there are no third-party servers where data is kept, using it for registration is safe. The CCPA, DSGVO, and GDPR are all followed while collecting data online. Anyone has also received certification for conforming to the worldwide ISO/IEC 27001:2013 information security standard.
Tourism and Hospitality Industry
The tourism sector has grown in popularity as a target for hackers in recent years. Several prevalent forms of internet fraud in the market include:
Breach of Data by Online Booking Platform
A data breach is a security issue when cyber attackers access online booking platform users’ sensitive information. The renowned travel agency Orbitz disclosed a security compromise in late 2017 in 2018, and the problem made thousands of consumers’ credit cards and other sensitive information vulnerable.
A similar occurrence took place in April 2019. When ransomware struck the Cleveland Hopkins International Airport, email systems were shut down, and some screens were destroyed.
Details of Stolen Payments
One of the expanding trends in travel fraud is the theft of a traveler’s credit card information. To steal credit card data, hackers build several forms of malware. According to PYMNTS’s investigation, fraudsters buy plane tickets or vacation packages before attempting to charge them back to their credit cards. Hackers have been known to exploit stolen payment information to make online travel reservations and resell those reservations to others for less money.
Hotel Rates Increase
According to the American Hotel & Lodging Association’s research, $5.2 billion was spent on erroneous and deceptive hotel reservations in 2017.
It’s a con artist’s go-to tactic for getting websites and businesses that facilitate internet travel into difficulty. The fraudster and the hotel work together to commit this kind of scam. When a hotel increases its rates, scammers will book rooms through an online travel agency using credit cards that have been stolen, and the travel agency will thus pay the chargebacks for the increased rate. In the travel business, identity verification can assist in preventing hotels from making bookings for fictitious persons using forged documents.
Identity-ID verification in the gaming industry
Although KYC regulations have been in place for online gambling for some time, there hasn’t been any regulatory oversight of the industry. Due to increasing pressure from activists, the general public, and gaming communities, gaming platforms are currently in a pickle: Should they impose strict customer onboarding requirements to confirm players’ identities and run the risk of losing clients who choose to provide identification proof? When there might be a negative effect on their reputation, business disruption, and gaming experience, can they afford to not? The most pressing question ought to be.
Is it conceivable that in the future, gaming platforms will be the target of regulators, and they will demand that all gamers have their identities verified? This level of accountability would, of course, prohibit minors from accessing certain games or making online microtransaction purchases, in addition to acting as a deterrent to gamers engaging in destructive behavior. PEGI specifications could determine these restrictions. KYC checks may also be used to prevent money laundering.
How Gamer Identity Verification eliminates Player Risk
Steam and PSN, among other platforms, may act as “hotbeds for radicalization,” according to new research by the Radicalisation Awareness Network of the European Commission. Indeed, because it has become more challenging to do illicit business through suppliers of financial services, criminal organizations have begun looking for new ways to conduct it, such as through schemes involving renting holiday properties.
Due to the growing popularity of microtransactions and the potential for money laundering, authorities may seek KYC norms in the industry very soon.
Criminal organizations are constantly seeking new sources of income, and online gaming payment systems have become a top target.
The use of virtual currency for in-game purchases, both convertible and non-convertible, has shown to be a viable technique for money laundering due to the lack of legislation requiring identity verification.
Research indicates that carding, a kind of credit card fraud in which stolen credit cards are used to make purchases on gift cards or charge prepaid cards, and money laundering use Fortnite regularly. Fraudsters will buy virtual money in-game by using funds gained unlawfully to buy in-game goods, and they will ultimately sell the goods for “clean” money.
After Valve disclosed that “virtually all” of the microtransactions in Counter-Strike: Global Offensive was being used for money laundering, commerce between individual accounts had to be stopped. The question is not whether government officials will consider the video game industry but when.
Insurance and Finance
Banks, credit unions, insurance companies, credit card issuers, accountancy firms, and more are all part of the financial services sector. These institutions benefit from increased production, efficiency, and customer satisfaction because of digitalization. Sadly, thieves are now using technology to exploit gaps in banking services and carry out financial crimes.
Cybercrime
Only the financial services industry accounted for over 62% of data breaches in 2019. The industry’s data breaches were caused mainly by hacking and malware assaults. The two most significant hazards for clients utilizing any online financial service platform today are the disclosure of private information and financial loss.
Regulatory Conformity
Online banking, cryptocurrency exchanges, and other financial services have all been widely utilized for tax avoidance and money laundering. As a result, law enforcement agencies have mandated that financial services companies follow KYC (Know Your Customers) and AML (Anti Money Laundering) requirements. Unfortunately, most companies don’t employ the proper technologies to adhere to these regulations, which increases online fraud.
Twelve of the top 50 banks in the world received fines in 2019 for breaking KYC and AML regulations. The French Criminal Court has imposed a $5.1 billion sentence on the Swiss bank for AML violations.
Identity Theft
The financial services sector’s firms are very concerned about identity theft. Online scammers employ various techniques to access consumers’ personal information and generate false financial benefits. One frequent kind of financial identity fraud is when criminals use your credit card information to make unauthorized purchases. Hackers may occasionally use your personal information to apply for new credit cards and loans.
Identity Verification in the Financial Services Sector
Information security heavily relies on identity verification and is beneficial in combating online crimes like money laundering and identity theft. Real-time digital identity verification tools may examine individuals’ prior records from databases and validate any identification paper.
Identification verification ensures that a user’s or client’s identity matches the one it should. Identity verification, commonly known as the KYC procedure, has become a requirement for companies involved in the financial services sector in most nations. For this reason, the market value for identity verification has grown significantly. By 2027, the identity verification industry is projected to generate 18.12 billion US dollars in sales, according to Statista.
The identity theft statistics shown below make it very evident how vital identity verification is in today’s world.
- The Federal Trade Commission (FTC) estimates that around 9 million Americans report identity theft yearly.
- The three most typical forms of identity theft are phone fraud, loan and lease fraud, and credit card fraud.
- The countries with the most significant rates of identity theft in 2018 and 2019 were the United Kingdom, Denmark, and Ireland.
- 56% of Europeans encountered at least one sort of identity fraud in 2018 and 2019, according to a survey from Finance.se.
Crypto Exchange
While cryptocurrencies like Bitcoin, Ethereum, and Dogecoin are getting increasingly popular, the market is still relatively young. As a result, as financial sector authorities examine and scrutinize the operations of cryptocurrency exchanges and other crypto businesses to stop money laundering and identity theft, regulation of the cryptocurrency industry is continuing to grow.
Unfortunately, fraudsters’ interest has grown tremendously along with some cryptocurrencies’ worth in recent years. With consumer demand rising quickly, vast sums of money being transferred internationally, and authorities lagging, it has produced an almost ideal environment for identity theft and money laundering.
By setting up new accounts using false identities and assuming the identities of others to take control of existing accounts, fraudsters have taken advantage of holes in the security of cryptocurrency exchanges to empty wallets of all available funds. Crypto exchanges and other cryptocurrency businesses have been quick to recognize the need for more security and regulation, given the scope and sophistication of these assaults.
Cryptocurrencies are now subject to further regulation. This implies that several anti-money laundering (AML) and know-your-customer (KYC) laws must be followed by businesses that let individuals and businesses acquire and trade cryptocurrencies. This implies that crypto exchanges and other businesses operating in the space must immediately adjust.
Requesting users to submit a copy of their ID, a photo of themselves, or their signature is no longer adequate. They can be forged with photographs taken from social media or personal information posted on the dark web, in addition to not meeting KYC and AML regulations.
To ensure the legitimacy of its users and protect their assets, cryptocurrency firms must use more reliable identity verification techniques. While ensuring regulatory compliance is an important goal for many businesses in the cryptocurrency industry, it’s equally crucial to provide consumers with a convenient experience when they are opening accounts, signing in, or completing transactions. There needs to be equilibrium.
Why is identity verification necessary for Crypto Exchanges?
Fraudsters are increasingly targeting cryptocurrency firms by assuming fraudulent or stolen identities. Payment card fraud, phishing scams, and transfer fraud are some of the most frequent dangers businesses in the cryptocurrency sector are now experiencing. An increasing number of fraudsters are also utilizing account takeovers to pretend to be legitimate users to steal money or transfer illegal funds.
Because some users feel less secure purchasing and trading cryptocurrencies, this, in turn, is eroding trust and hurting growth. According to the GBG State of Digital Identity survey, one-third of customers think their personal information is for sale, and two-thirds are worried that it may be revealed when they make purchases online.
Digital identity verification is a crucial tool in the armory of crypto firms fighting fraud because it gives them the data they need to swiftly identify and deter fraudsters at scale while still offering the user-friendly and safe experience customers have come to expect when trading online.
Ever wonder what types of fraud are concealed by these “earn money from home” advertisements?
You’ll be asked to join their service after getting a referral link, so consider that. You must submit a few papers to join this elite group, and you’ll get your free $150 after submitting your ID information.
One peek at the mandatory fields is all it takes to see what’s going on: Your ID documents are effectively purchased through the service.
Techniques for Identity Verification
Ever wonder what types of fraud are concealed by these “earn money from home” advertisements?
You’ll be asked to join their service after getting a referral link, so consider that. You must submit a few papers to join this elite group, and you’ll get your free $150 after submitting your ID information.
One peek at the mandatory fields is all it takes to see what’s going on: Your ID documents are effectively purchased through the service.
How are they $150 worth? Well, scammers and other bad people are becoming increasingly interested in these documents. In this piece, we’ll examine the multiple methods they obtain, how they’re used, and why identity proofing is more crucial than ever in the internet world.
Identity Verification Methods
When someone makes a purchase, submits an application, or engages with something that requires some level of verification, identity proofing is the process of confirming that person’s identity.
The organization can now carry out KYC checks in a far more user-friendly way thanks to biometrics, video identity verification, and other contemporary technology. Previously, consumers frequently had to provide physical identification papers for verification purposes.
It’s necessary for fraud prevention and a regulatory requirement in some areas (banking, fintech), but the lengthy procedure might drive away customers.
Resolution, Validation, and Verification are the three main components that remote identity proofing needs to provide complete protection, according to the US National Institute of Standards and Technology.
- The identity resolution approach is the process of identifying a user’s identity inside a customer database, population, or any user-based system.
- An identity validation mechanism is used using a password or other specific information from the person.
- Before concluding that the evidence presented is consistent with the data supplied, use an identity verification approach.
What Makes Identity Verification Important?
Identity proofing is crucial for organizations that want to expedite their onboarding procedures since it helps to verify that only reliable users have access to any data or goods. This extra layer helps to safeguard businesses and their users from fraudsters.
Scenarios consist of:
- KYC Verification: Financial firms, for example, are obligated under Know Your Customer policies to verify the identity of their users.
- Electronic credit scoring: A loan provider would similarly have to create a user profile based on user IDs.
- SCA/PSD2: Strong Customer Authentication intends to strengthen checks against stolen authentication components and is advised by the PSD2 guideline.
- AML: Document verification is also necessary for anti-money laundering inspections, which are common in iGaming and forex exchanges, among other places.
- Fraud prevention: one technique to identify fraudsters is verifying your user’s identity. By doing so, transaction fraud and subsequent chargebacks are decreased. If you flag a questionable login attempt, you can verify the individual’s identity. Similarly, unusual online activity (such as significant cash deposits and withdrawals) may necessitate an additional verification step.
Limitations of Existing Identity Proofing Tools & Software
What, then, should an Internet company do if they wish to confirm a person’s identity? Of course, they can have the data manually reviewed by internal or external staff.
API-based solutions are another option. The issues? These inspections are costly and slow down legitimate consumers’ customer journeys. For instance, every document check with an outside provider will cost about $2.
Additionally, ID verification systems have expenses that are more difficult to quantify but less critical regarding user friction. A seamless user experience is increasingly a competitive advantage in the digital era.
By serving as an addition to your already-existing to your customer’s invisible criteria, IDcentral assists in weeding out possible fraudsters before KYC. All checks are done in real-time.
Businesses that increase user friction at any point (onboarding, logging in, or money withdrawal) risk driving customers away and toward rivals.
Last but not least, even if you go through a laborious identity-proofing procedure, there’s a potential that mock papers, synthetic identity frauds (which combine actual and made-up client data), and stolen IDs will still be able to trick your system.
Balance security and friction
Security and friction must frequently be balanced in online enterprises. If there are too many barriers to authentication, people will search elsewhere. If there are too few, con artists might deceive your employees into benefiting their business.
Adding an unseen layer of security to your website may improve your informed assumptions about your users.
Data enrichment can specifically assist with this, enabling you to carry out a thorough digital footprint study. You may do it instantly without deterring loyal clients who can contribute to your company’s financial success.
Technologies
One of the most significant technological developments that exist now is digital identification. The way individuals engage with both public and private institutions has changed as a result. How about digital identity, however? It is a collection of digital credentials and traits that have been verified; it is not dissimilar to how people identify themselves in the actual world. It contains details such as a unique identity number, a name, a location, a date of birth, citizenship, and biometrics, among other things. Digital identifiers differ between nations. Germany, Italy, Spain, and Portugal have eID cards, Finland, Belgium, and Estonia have mobile IDs, and India has Aadhaar cards, which include a particular biometric-related ID number. The world’s most extensive biometric ID system, called Aadhaar, assigns Indian people a 12-digit unique identity number. To make sure that the underserved population obtains the promised benefits, UIDAI was established. However, since its debut in 2009, it has evolved into a versatile tool for identity verification nationwide. Today, Aadhaar cards are nearly universally used as primary identification in India. Aadhaar is incredibly important for identifying in India, but since the epidemic, its use as a digital ID for verification has multiplied.
In light of social-distancing norms, the COVID-19 pandemic breakout in 2020 prompted several public and commercial entities to adopt digital means for identification verification. Digital onboarding procedures emerged as a result.
Digital onboarding was an option in the past. Digital onboarding became essential due to the pandemic, which increased the usage of digital identities. Digital procedures were adopted by all corporate and governmental organizations, revolutionizing the connection between businesses and customers. It made it possible to evaluate people online by electronically validating their legal papers.
Here are seven game-changing digital identity developments to watch in 2022 and beyond:
Face Liveness Detection
For several reasons, facial biometrics are used to determine if a person is whom they say they are. Facial liveness detection, on the other hand, determines whether the individual is alive. Liveness may identify a user’s credentials and physical location using a camera-enabled phone, computer, tablet, or other camera-enabled devices. The whole identification procedure is digital and conducted online, and it employs a machine learning algorithm to allow businesses to determine clients’ legitimacy swiftly. The primary goal of authentication is to provide a high-quality, rapid, and secure consumer experience.
Face Match Technology
Face matching, in which businesses compare the faces in the photos on government-issued IDs with the individual’s selfie, is another new development in digital identity. It made it possible for businesses to identify customers digitally without requiring a physical presence. Additionally, businesses are employing face-matching to verify numerous papers, and a quick and straightforward online approach is available.
Digital KYC Verification
There is a digital KYC process available online for those who need to comply with KYC requirements but still wish to complete their required KYC procedure. It is a solution that regulatory organizations often embrace, and it ensures rapid onboarding by doing a KYC validation check and a liveness check on a user.
Thanks to digital KYC, users may become KYC-compliant while lounging in the comfort of their homes. Electronic papers and signatures are required to make the KYC verification procedure more convenient.
Biometric-based KYC with validation
Biometric validation-based KYC is expanding to combat fraud and identity theft. Individuals are linked to their digital identities via biometrics. Governments and organizations may rapidly identify the right individuals and offer them services by employing a simple fingerprint or IRIS scan of a consumer and a unique ID.
Digital is the future and digital procedures are the USPs in this online environment. Trends in digital identification are quickly changing how businesses and agencies carry out verification procedures. The days of many appearances and house visits are long gone.
We will witness a surge in more instantaneous and safe digital identification trends as there is a greater desire for seamless experiences and smoother onboarding procedures.
Benefits
We already know the real-world advantages of using digital processes over traditional ones, not simply because the influx of new tools and technology has made it an effortless procedure but also because you can start conducting risk-assessed identity verification for new consumers.
Maintain & Enhance your reputation through better Customer Experiences
The reason Airbnb has become so popular is that it holds everyone accountable. Due to the requirement that both guests and hosts confirm their identities and keep positive ratings, there is an implicit trust on all sides. The importance of reputation must be balanced for companies of all sizes. People may easily switch brands if they are still waiting to receive what they want in the modern day due to the abundance of customer options.
On top of that, people actively seek out companies they can depend on, making trust more crucial than ever. Customers demand assurance that their information is secure during frequent data breaches. Running identity verification checks demonstrates your commitment to fostering trust in the increasingly dangerous internet environment.
Any connection must be built on trust, particularly in the inherently unstable digital environment. If they don’t feel as though their requirements are being addressed or that the service being offered meets their standards, they can—and often do—move on to other businesses.
Recognizing this need for customer and brand trust may ensure a company’s income and image are maintained. On the other hand, improving your reputation and giving clients the confidence they require to use or continue to use your business work wonders for your financial position.
Quickly confirming a customer’s identification contributes to building that crucial trust.
For this reason, many businesses use verifiers to handle the identity verification process using client documentation, face-matching selfies, and KYC watchlist checks. Implementing third-party validator speeds up the process by keeping customer checks on file and enabling businesses to continue onboarding consumers without spending valuable time fact-checking papers themselves.
Frequently paraphrased: “When clients develop an emotional bond with a company, they become advocates, promote the brand and wish your company well in addition to doing so. People want customer-centric companies to succeed because they know how tricky business may be right now.
By implementing an easy identity verification procedure, you may allay customers’ rising fears and demonstrate your care for their safety. Then, the seeds of trust will start to germinate and flourish. Utilizing KYC demonstrates your concern for your customer safety on your platform.
Avoid Expensive Fines
The banking sector will be hit with fines totaling $10.6 billion in 2020 for failing to comply with anti-money laundering (AML), know your customer (KYC), data protection, and MiFID requirements. 99% of the total enforcement actions imposed in 2020 will be financial penalties for AML-related compliance violations. One of the biggest banks in Australia, Westpac, agreed to pay a record AUD 1.3 billion ($959 million) punishment for violations related to money laundering. The fact that most firms cannot afford a fee of this magnitude underscores the need for AML and KYC procedures.
AML refers to a group of rules, laws, and protocols created expressly to prevent the practice of reporting money earned illegally as legitimate revenue. This is related to the requirement for KYC, which companies use to identify their clients and determine the likelihood of illicit activity.
If you don’t follow these rules, you risk paying expensive penalties or, in the worst-case situation, going to jail.
Businesses that employ them avoid any possible fines since using simplified, effective identity verification software and procedures comply with AML and KYC standards.
Depending on their location and clients, businesses may also be subject to several specific laws and standards.
More than 90 nations today mandate that companies confirm the identities of their clients and maintain that information for a specific period.
This is a part of a larger initiative to stop money laundering, terrorism, and other crimes around identity theft. Keep in mind that these guidelines are continuously being revised and modified, so it’s essential to remain up to speed to ensure you’re not breaking any laws.
Prevent expensive chargebacks
Every year, a sizable percentage of all identity fraud instances involve credit card fraud. Since most transactions now fall under the “card-not-present” category, it has become much simpler to perpetrate fraud since companies have started enabling their consumers to use credit cards for online purchases.
Consequently, individuals would purchase products online using stolen credit cards, and whenever the valid owner of the card learned about it, they would cancel the transaction. The company would be required to repay the money if the original fraudster could not be located and identified.
In the financial industry, this is referred to as a chargeback.
Sadly, they may be an expensive aspect of doing business for businesses that take credit cards (with fees, operating expenses, and customer acquisition costs, companies often lose 2 to 3 times the amount of a refundable transaction.)
This is stopped in its tracks by identity verification, which thoroughly verifies each consumer.
Many firms may avoid expensive chargebacks by simply updating their identity verification procedures for card-not-present transactions to include one or more identification methods (for example, facial recognition or a two-step verification process).
Tighter verification procedures can also end instances of “friendly fraud.”
This is when well-intentioned customers request a chargeback from a firm rather than a standard return after purchasing from them. They need to consider its potential impacts on the company to believe it is just another means to get their money back.
Chargebacks allow other, less charitable customers to receive something for nothing.
They keep submitting chargeback requests while claiming to have never received an item. Identity verification makes it impossible for “internet shoplifters” to operate anonymously, which can reduce the number of friendly fraud instances.
Avoid worries about fraud and money laundering.
We previously discussed Standard Chartered receiving a hefty fine this year for money laundering. Most businesses, especially those with limited incomes, are concerned about receiving a fine of this magnitude.
No of the size of the firm, even the slightest suspicion of money laundering can lead to its demise. To determine which users may be at high risk, enterprises are increasingly moving toward employing risk-based models that combine identity verification.
Based on the potential risk of specific transactions, they can utilize this information to develop authentication tiers (and then mark those that are good and those that might be fraudulent accordingly).
As the corporate environment becomes more and more computerized, this is becoming more and more crucial. Creating digital trust involves, among other things, making sure that consumers are whom they say they are.
Many companies use two-factor authentication, which requires customers to present two kinds of identification, such as a passport, bank card, or face for facial recognition, to prevent fraud and money laundering activities.
ATMs serve as the most straightforward illustration of two-factor authentication in operation. To withdraw money, customers must have their PIN and bank card, which serve as two forms of identification.
Companies are forced to reconsider their identity verification procedures to make them more internet-friendly as more transactions occur online.
Enhance the client experience
Customer experience has been chosen as the most exciting business prospect for the upcoming years, as seen in the graph above.
Consumers today want a customer-centric experience from every company they do business with, and a great user experience works to remove any hurdles customers may have while streamlining procedures.
When referring to effective identity verification procedures, the term “frictionless” is frequently used; this refers to getting information about the consumer directly from sources other than the customer.
As a result, you may develop a smooth, digital workflow that does away with the majority, if not all, of the requirement for manual entry and paperwork that frequently requires several days to handle.
Customers benefit from a more seamless onboarding process, and more significantly, they may immediately utilize your good or service.
Customers don’t have to wait hours or even days to get started thanks to the integration of biometric solutions and digital identity verification techniques like face recognition, automated scanning, and liveness detection.
The identity verification procedure for most firms resembles something like this:
- Step 1: compile identification papers such as passports, ID cards, or licenses
- Step 2: confirm the legitimacy of the identification papers.
- Step 3: Create a report for auditing purposes
- Step 4: After performing customer authentication in Step 3 ensure the person providing the ID is the same person the ID refers to.
Although this approach is good, processing the papers might take some time, especially if everything is done manually.
It is far easier to switch to a digital procedure since identification checks may be completed virtually instantly in the background, meaning customers don’t have to wait.
A well-oiled, nearly instantaneous procedure like this may significantly boost conversion rates. A positive client experience encourages repeat business and refers to streamlining procedures so that more people are likely to complete them in the context of identity verification.
Current State of Identity Verification Solutions
Identity theft and cyberattacks are rising, fueling the market’s expansion for identity verification. Computer networks and digital data are increasingly being used by businesses to manage their day-to-day operations and activities. A surge in cybercrimes allows thieves to breach highly developed and sophisticated bank accounts and use the credentials they steal to create interest payment accounts, online merchant accounts, and phony mobile phone accounts.
Several firms increased their identity verification procedures during the COVID-19 outbreak to protect clients from fraud. For instance, 72% of online marketplaces have increased their deployment of ID verification technology during this worldwide epidemic, according to a report.
Adopting solutions impact the market’s expansion through strict regulations and compliance requirements. Compliance with know-your-customer (KYC) and anti-money laundering (AML) regulations has come under increased scrutiny from regulatory bodies. With a compound annual growth rate (CAGR) of 17.1%, the identity verification industry is predicted to increase from $8 billion in 2021 to $17.7 billion in 2026.
Large-scale, rapid changes in end-user behavior have undoubtedly presented new difficulties for organizations, such as increasing the frequency and sophistication of identity theft cyberattacks and effectively managing the lifetime of digital identities throughout the customer experience.
These issues were the main topic of the most recent Mitek Red Point event in Spain, where guests had the opportunity to participate in a live discussion with industry experts on the future of the global digital identity market and the function of biometrics in the customer life cycle. According to experts, the top 13 trends in identity verification for 2022 are listed below.
- We now spend our daily lives with the idea of the digital ID. Nowadays, it is more crucial than ever that technology enables users to authenticate themselves and show that they are trustworthy.
- What constitutes a digital identity has expanded in scope. A digital user is now more than simply a number; they have a sophisticated collection of features that make it possible to identify them without a doubt, such as their network activity or biometric traits.
- Businesses are altering how they perceive and handle digital identities. It involves all aspects of the firm strategically rather than just a function that depends on departments like IT.
- Legislation and technology still need to be in sync. Strict laws must advance quickly to cover all the sectors affected by technology. Although there has been advancement in the protection of user data, there has yet to be much thought put into designing a user interface that conforms with legal requirements for electronic payment processing.
- People desire greater security and openness. Users are eager to share their information during identity identification as long as they know it will be handled responsibly. They want to know how it will be used, why it is needed, and what security safeguards the business has to keep it safe.
- There will be a massive increase in investments in technology that facilitate the decentralization of information. By 2025, it is anticipated that blockchain technology would have grown by 60%. The present issue is that governments do not perceive decentralization as a danger but rather as an opportunity.
- Digital identity verification continues to be plagued by a general lack of confidence. Most users, including individuals, businesses, governments, and public administrations, continue to wonder how well-equipped organizations are to protect digital identities. The verification procedure is frequently seen as more of a hassle than a requirement to guarantee the security of the data or the transaction itself.
- If users understand why there needs to be friction in the user experience, they are more likely to accept it. Suppose a user understands why certain information or actions, like shooting a picture, are required as part of the registration or purchase process. In that case, it is simpler for them to tolerate some friction. A certain amount of friction provides perceived security, but it’s crucial to strike a good balance to prevent the experience from suffering. The amount of friction that should be applied to each process or activity must thus be determined.
- Blockchain is one of many new technologies people will use if it is reliable and stable. To regulate new technologies, make effective use of them, and be open to processing information, governments and businesses will play a crucial role. Understanding technology is essential before employing it, as is controlling who has access to it and how it is utilized.
- We can enhance digital security thanks to technological advancements, particularly in machine learning and artificial intelligence. However, they also pave the path for increasingly complex fraud and crimes, including deep fakes.
- Confirming a user’s identification via username and password is a highly unsafe practice. More sophisticated technologies are needed to uniquely identify the person on the other end of the screen, such as two-factor authentication or face or voice biometrics.
- Adopting digital ID verification systems will depend heavily on biometric technology like face recognition. Biometric identification is regarded as the most secure digital identifying method by 70% of enterprises. Multimodal biometrics, which refers to mixing two or more biometric elements in the verification process, is one of these technologies showing the most promise.
Verification trends will undoubtedly keep developing, advancing, and changing. Still, by paying attention to what the industry’s insiders say, you can remain ahead of the curve, pivot, and adapt in real time with them.
To find out more about experts’ opinions on each of the trends mentioned above – Request a Demo
Identity Verification and Digital Onboarding in 2023
The technological world and everything related to it move swiftly, and identity confirmation is no exception. To predict how businesses will confirm the identity of their consumers in 2023 and beyond, we are looking at five trends and problems in data security and privacy, fraud prevention, and laws.
Digital Identity to help forge Digital Businesses
In 2023, digital identity is expected to keep growing inexorably. The Covid-19 epidemic expedited this trend, which will continue to be the primary method of gaining access to banking, government, health, and other services and career and educational opportunities. This is anticipated to have a global market worth around $33 billion by 2025, a more than 100% growth from its value in 2020.
In 2023, the usage of digital identity wallets is also anticipated to rise. The number of onboarding situations where verification is necessary has increased to the point that repeating the same procedures for each service takes more time. As digitalization becomes, more widespread, more predicted verification methods are expected.
Utilizing a foundational ledger architecture, the Bring Your Own Identity (BYOI) paradigm will gain more traction. However, the market for these systems is still fragmented, with regional variances and no interoperability standards. However, if use cases develop more quickly over the coming years, a worldwide standard for portable decentralized IDs is expected to materialize.
Data privacy and security
The warning is clear: presumptively, everyone can access your personally identifiable information (PII). To impersonate somebody online and commit synthetic identity theft, stolen static identity credentials like names, passwords, and email addresses are utilized. Users are placing increasing importance on managing their data, with almost half prepared to spend time and money to improve privacy protection. Self-management of customer data, as provided by digital identity wallet solutions, also lessens an organization’s need to gather, handle, and protect personally identifiable information (PII), making the idea more acceptable to the corporate sector.
Increase in Fraud Attempts
The unpleasant truth is that scam artists profit when the economy is unstable. As the international cost of living crisis continues in 2023, ransomware, geographically-targeted phishing, assaults connected to cloud security, and IoT threats are all anticipated to rise.
Deepfake is one technique to keep an eye on in the next year. Millions of false identities might be manufactured by malicious actors utilizing deepfake technology as machine learning (ML) grows more proficient, and face databases store far more information about people’s likenesses.
Technology has also made it possible for various kinds of online fraud. Because the resources required to assume someone else’s identity are all available on the dark web, those looking to engage in illicit behavior no longer need to provide fake physical documents. Because fraudsters keep up with technological advancements as rapidly as they occur, it is difficult for suppliers of identifying services to create fraud prevention strategies. As the underlying AI ensures that the digital connection or transaction is with another person and not a fake, lifeless image or video, “liveness detection” helps in biometrics.
It will become increasingly crucial to distinguish between hazardous people and reliable customers across platforms as fraud and its attendant sophistication rise.
Regulation of cryptocurrency in India
If the adoption of digital identity concepts is to be encouraged, governments must establish well-designed legislative frameworks. Authorities must establish clear and consistent regulations for the collecting, processing, and sharing personal data. This is true for the cryptocurrency industry in particular.
After FTX’s implosion in November, the cryptocurrency sector had a terrible close to 2022. The European Union (EU) expects the expansion of the Transfer of Funds Regulation (TFR) to cover crypto assets to take effect in 2023, requiring the sender and beneficiary of all related crypto transactions to be identified.
Markets in Crypto Assets (MiCA), which has laid forth regulations for the creation, admission to trade, and management of crypto assets, has also been proposed as the first significant regulatory framework for cryptocurrencies. British suppliers who intend to conduct business with consumers from the continent must seek MiCA authorization, notwithstanding the EU’s enforcement. Although MiCA is anticipated to be implemented in 2024, British providers should prepare for the framework’s adoption commencing the following year.
Additionally, MiCA and TFR may significantly impact how cryptocurrency is regulated outside of the EU. Since the FTX disaster, other countries, including the United States, are now turning to Europe as a model for following regulatory frameworks and landscapes in the cryptocurrency industry.
Knowing your customer (KYC) will no longer only be a checkbox activity
KYC is anticipated to broaden in scope as it relates to consumers verifying their identities and businesses knowing who these customers are.
Silos-based work is no longer acceptable, and the quality of client service and satisfaction are seriously threatened. To improve departmental communication, businesses must embrace multipurpose IT solutions’ functionality. Their operations will be optimized as a result.
The sector of financial services and the organizations within it serve as excellent examples. The dots must be connected since several departments, including Compliance, Sanctions, and KYC, all operate on their schedules. The finest technology and KYC suppliers will know how departments interact with one another and facilitate multipurpose usage. As the work done by KYC influences how other departments, including fraud and other financial crime sectors, see criminals, this will have significant positive effects.
How IDcentral’s KYX solution uses customer-centric approach for KYC Verification
IDcentral’s flexible Digital Onboarding Solution comes integrated with the latest AI technology for accurate ID verification, precise Liveness Detection, and speedy Identity Proofing. Enable Remote-Digital Onboarding capabilities with our API based solutions which have variable levels of eKYC procedures according to your customer base and compliance requirements.
Try IDcentral’s KYX solution with AI-based Document Verification

Sumanth Kumar is a Marketing Associate at IDcentral (A Subex Company). With hands-on experience with all of IDcentral’s KYC and Onboarding Technology, he loves to create indispensable digital content about the trends in User Onboarding across multiple industries.
